How To Protect Your Bitcoin With Coldcard And Integrated Seed XOR

This guide demonstrates everything you need to know in order to secure your Bitcoin private keys using a Coldcard hardware wallet and its integrated Seed XOR method. With this method, you are able to split your backup seed phrase into multiple parts that look and function like complete 24-word seed phrases of their own. This opens up a range of possibilities and safeguards to protect your bitcoin.
Coldcard with Seed XOR opens up a range of possibilities to protect your bitcoin.
Background On Self Custody And Keeping Bitcoin Safe
Welcome to the wonderful world of self custody, this is where the laws of man and the laws of math collide in a battle over your cryptographically-secured wealth.
There are a number of different reasons that people find themselves here; some realize the risks associated with trusted third-party custodians; others know that authorities have what it takes to take what you have; and a few understand that inflation is taxation without representation and confiscation of wealth without due process of law, propped up by an elaborate scheme between the U.S. Treasury and the Federal Reserve in an attempt to keep the rich in power and everyone else enslaved to debt and perpetual consumption.
For whatever reason you found yourself here, let’s dive into securing your bitcoin in a way that offers protection from environmental hazards, confiscation and seizure, that mitigates trust and introduces plausible deniability. You can find further background on Seed XOR here.
This guide starts with an initial set up section for new users. If you already have a Coldcard setup, then you can skip straight to “Step Seven: Splitting The Seed Phrase With Seed XOR.”
Step One: Materials
Although there are several hardware wallets to choose from, you can see my top-10 reasons for using Coldcard here. At a bare minimum to follow along with this guide, you will need:
One ColdcardThree stainless-steel SeedPlatesOne spring-loaded punchOne ColdPower AdaptorOne microSD CardOne USB-to-micro-USB cableOne permanent markerOne penOne balanced diceOne nine volt batteryOne wallet backup card (included with Coldcard)One computer with internet connection
At a bare minimum to follow along with this guide, you will need these items.
If you haven’t done so already, you can order a SeedXOR kit from Coinkite that comes with a Coldcard, an industrial microSD card, three stainless-steel backup plates, and the security bags.
Step Two: Checking Your New Coldcard
Upon receiving your Coldcard, ensure that the tamper-evident bag has not been compromised. If anything seems amiss or if you have any problems, contact support@coinkite.com.

You will see the tamper-evident words “void” appear when the seal is opened.
You will see the tamper-evident words “void” appear when the seal is opened.
Inside, you will find your new Coldcard, the wallet recovery backup card, sticker(s), and an additional copy of the bag number which should match the bag number printed on the outside of the bag.
Inside the bag from Coinkite.
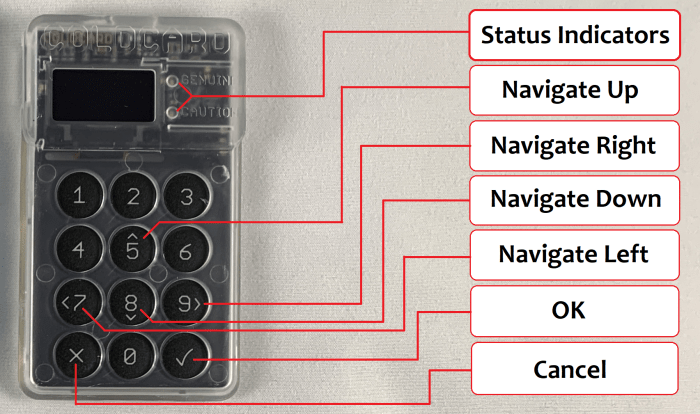
Here is a graphic to help you figure out the navigation of your Coldcard. You can always hold down the “up” or “down” arrows when scrolling.
Figure out the navigation of your Coldcard.
Step Three: Upgrade Firmware
One of the best features of the Coldcard in my opinion is that it can be used in a completely air-gapped fashion, meaning that you never have to connect it to a computer, although that option is there if you choose to use it. I prefer to use a nine volt battery with the ColdPower adaptor.
Using Coldcard in a completely air-gapped fashion.
First, read and accept the terms of sale and use. Then you will be asked to confirm the bag number. If there are any discrepancies, contact support@coinkite.com.
You will be asked to confirm the bag number.
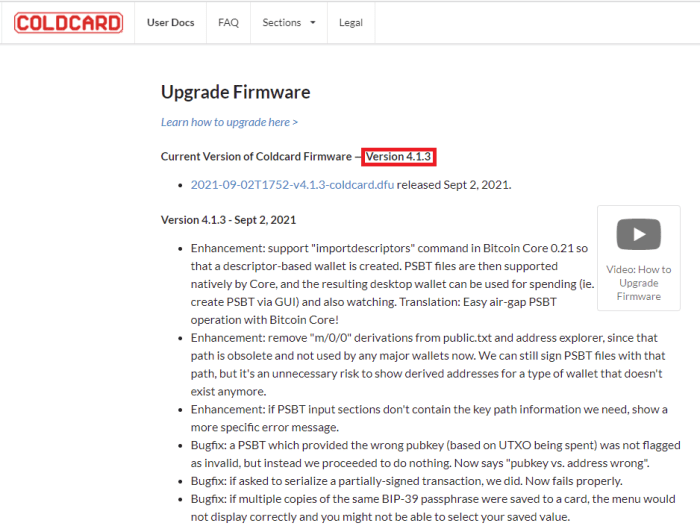
Next, select “Advanced” and then scroll down to “Upgrade Firmware” and finally “Show Version.” If your displayed firmware version is older than the most recent version available on the Coinkite website here, then follow the next steps to upgrade.

If your displayed firmware version matches the most recent one, then you can skip down to Step Four: Setting A PIN.
Source: https://coldcard.com/docs/upgrade
Even the firmware can be upgraded in an air-gapped way by utilizing the microSD card. These steps will show you how to do that and verify the integrity of the firmware file on a Windows desktop using Kleopatra OpenPGP from the GPG4win bundle.
If you don’t want to get into the PGP verification piece of this process, then you can skip ahead to the part about just saving the firmware file to the microSD card and loading on the Coldcard.
These next steps will show you how to save the PGP-signed hash value of the .dfu file and verify it with Doc Hex’s PGP public key and then calculate your own hash value on the firmware to confirm.
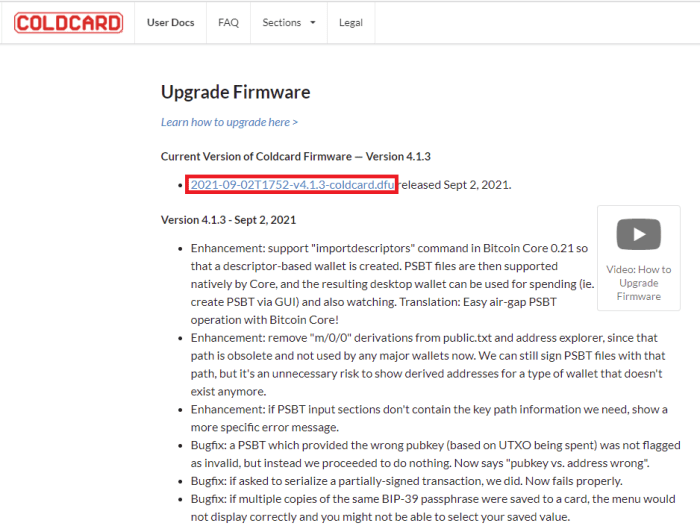
From the CoinKite website, click on the link for the latest firmware version at the top of the page. This will automatically download a .dfu file.
Source: https://coldcard.com/docs/upgrade
From this same page, scroll down toward the bottom to the advanced section and then click on the “this clear-signed text file” link. That link will open a PGP-signed message containing the SHA-256 hash values of various firmware versions.
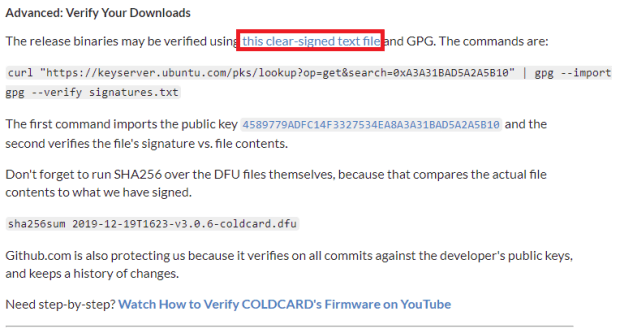
Source: https://coldcard.com/docs/upgrade
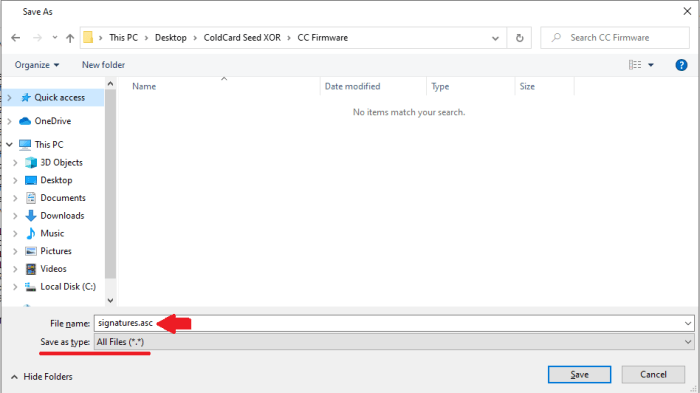
You want to save this PGP signed message as a .asc file. You can just hit “ctrl” and “s” from your web browser and you should be presented with a pop-up window like the one below. Make sure you have the “All Files (*.*)” option selected from the “Save as type:” drop-down menu. And then save the file with the “.asc” extension. You can leave it named “signatures.”
You can leave it named “signatures.”
Next, you need to get Doc Hex’s public PGP key and import it to your Kleopatra keychain so you can certify it. Doc Hex’s public key can be copied from this keyserver here.
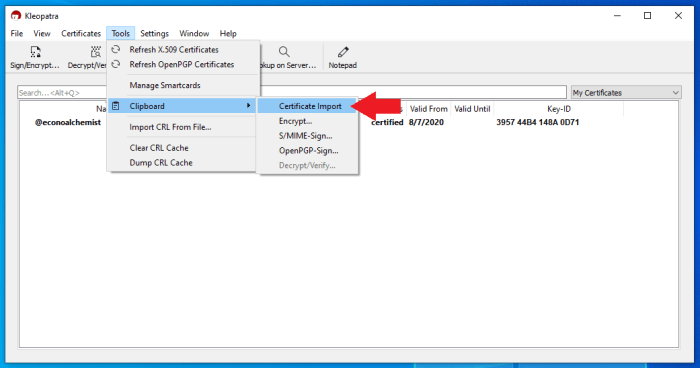
Once you copy his public key to your clipboard, then in Kleopatra navigate to “Tools,” then “Clipboard,” then “Certificate Import.” You will then be asked for your PGP password to certify Doc Hex’s public key. Once certified, this public key will be added to your keychain.
Once certified, this public key will be added to your keychain.
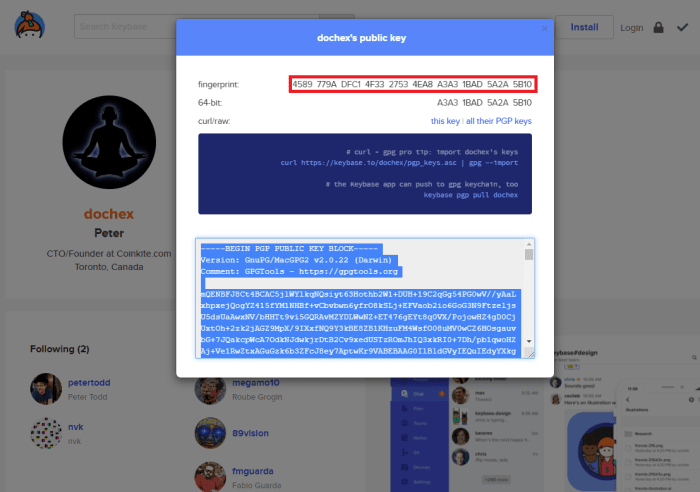
You can confirm that the fingerprint of the public key you just imported for Doc Hex matches the fingerprint of the Doc Hex account from KeyBase here.
Source: https://keybase.io/dochex
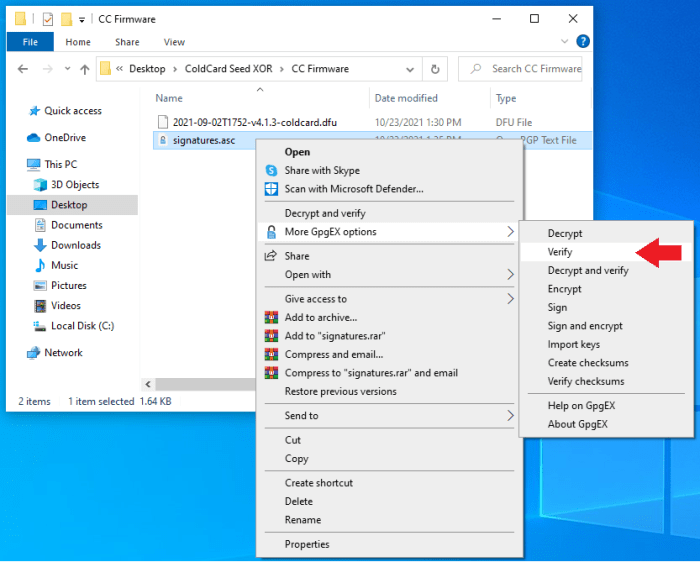
Now that you have Doc Hex’s key imported and certified, you can verify that the signed message with the firmware hash values was actually signed by Doc Hex. Open the folder containing the signed message .asc file and right click on it, then select “More GpgEX options,” then “Verify.”
Open the folder containing the signed message .asc file and right click on it, then select “More GpgEX options,” then “Verify.”
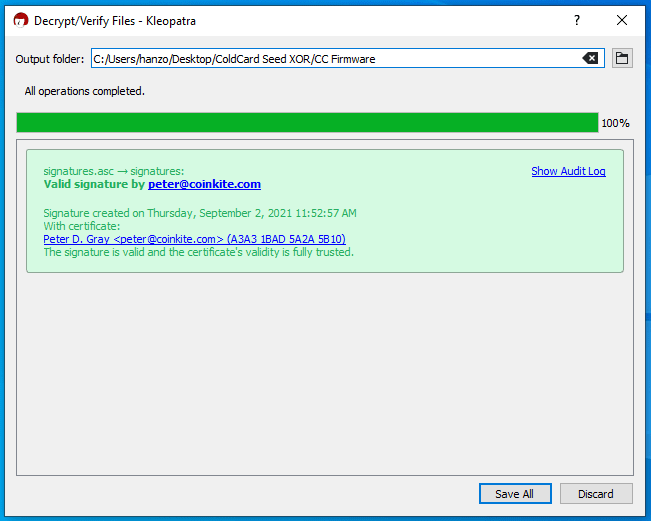
Kleopatra will start calculating the veracity of the signature and after a moment, you should receive a dialog box confirming that the signature matches the public key you certified.
You should receive a dialog box confirming that the signature matches the public key you certified.
At this point, you have verified that the PGP-signed message containing the hash values for the firmware files was in fact signed by Doc Hex. But you now need to verify that the .dfu firmware file does in fact return the same hash value as the one in the signed message.
To do this, I prefer using a freeware hex editing program called HxD. Simply navigate to “File” then select “Open” and navigate to the file path where you have the firmware .dfu file saved. Once opened, then navigate to “Analysis” then “Checksums” then scroll down to “SHA-256” and hit “OK.” Then the software will return the calculated SHA-256 hash value on the firmware file you downloaded. Visually compare this returned hash value with the hash value that you can look at in the signed message by opening it with a text editor.
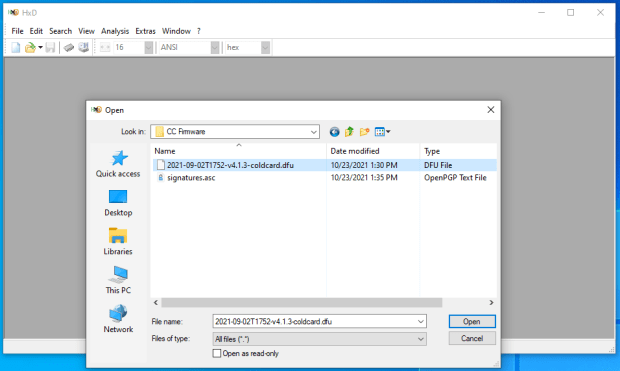
Now you know that the firmware file you downloaded is an exact match to the file that Coinkite intended that you receive and that it is safe to install on your new Coldcard.
Grab your microSD card and the USB adapter and insert them into your desktop. Once recognized, just drag and drop the firmware .dfu file onto the microSD card. Then safely eject the microSD card.

Turn the Coldcard over and insert the microSD card into the slot until it clicks in place.
Insert the microSD card into the slot until it clicks in place.
You should still be in the “Advanced” menu, then scroll down to “Upgrade Firmware” then “From MicroSD” then select the firmware file. This will take a moment to automatically load, verify and upgrade.

With the firmware now upgraded, you’re ready to move on and set your PIN number.
Step Four: Setting A PIN
Make careful considerations with your PIN number. You don’t want to use one that is easy to guess. It is convenient when you can memorize it so that you don’t have to find your notecard or other storage medium every time you want to access your Coldcard. Or perhaps you want a PIN that you don’t have memorized, specifically so that you must have access to your notecard or other storage medium to open the Coldcard.
Either way, your PIN will have two parts: a prefix and suffix. The idea is that once you enter the prefix, you will be presented with two anti-phishing words. If the words are the same as the words that were originally presented to you at initial startup, then you know that your Coldcard has not been tampered with since the last time you accessed it.
First, select “Choose PIN Code,” then you will see a brief description of how the PIN code works. Each part of your PIN code can be between two and six digits. There is absolutely no way to access a forgotten or lost PIN. And if you enter a PIN incorrectly too many times, it will brick your Coldcard as a security feature.
First, select “Choose PIN Code,” then you will see a brief description of how the PIN code works.
After hitting “OK” you will get one more warning about the risk of losing or forgetting your PIN. After reading that, you can enter your PIN prefix. Use the included notecard to write down your PIN prefix, then hit “OK.”

Next, you will be presented with your two anti-phishing words. Write these down on your notecard.
You will be presented with your two anti-phishing words. Write these down on your notecard.
Next, enter your PIN suffix, then write it down on the notecard and hit “OK.”

Then, you will be asked to re-enter your PIN prefix, confirm the two anti-phishing words, and enter your PIN suffix. The Coldcard will save that information and then open up the wallet where you can generate your seed phrase.
Step Five: Creating A Seed Phrase
There are a couple considerations you may want to make when creating a seed phrase.
For example, Coldcard will generate a seed phrase for you by default, but maybe you don’t trust the true random number generator (TRNG) used for some reason. Well, you don’t have to trust it because you can generate your own entropy with dice or by other means. Then you can leave the seed phrase like it is, with 24 words, or you can add a 25th word, also known as a passphrase.
The passphrase can be any combination of upper case letters, lower case letters, numbers, or special characters. There is no way for the wallet to know if your passphrase is correct or not though once you set it. So if you do decide to use a passphrase and then you misenter it when accessing the wallet in the future, the Coldcard will display a perfectly valid wallet, but it won’t be the wallet that contains your funds. Even with the same 24 words, entering two different passphrases will generate two completely different wallets.
So, think about what your threat model is, how you will secure your recovery information and how your loved ones would recover your bitcoin if you were gone.
Typically, I like to use dice to generate my seed phrases and then I like to add a high-entropy passphrase to it, so I will show you how I do it and you can pick and choose what works for you.
Like I said, the Coldcard will use a TRNG to make a random seed phrase for you by default. Select “New Wallet” and after a moment you will be presented with 24 words. You can use that seed phrase if you want, there is nothing wrong with doing so.
Select “New Wallet” and after a moment you will be presented with 24 words.
But I like to scroll down to the bottom of the word list and select “4” to add some dice rolls.
Scroll down to the bottom of the word list and select “4” to add some dice rolls.
It is recommended to use at least 50 dice rolls for 126 bits of entropy or 99 dice rolls for 256 bits of entropy. Entropy is calculated by using: log2(6) = 2.58. For reference, it would take the world’s most powerful supercomputer trillions of years to brute force a 256-bit key.
So, roll the dice and enter the corresponding number for each roll. Repeat this process as much as you want. If you roll fewer than 50 times, then the Coldcard will add the remaining necessary entropy with the TRNG. Then hit “OK.”

You can always verify that the dice roll math is actually doing what it purports to be doing by following the instructions in the Coldcard documentation here, or by checking out another guide of mine here.
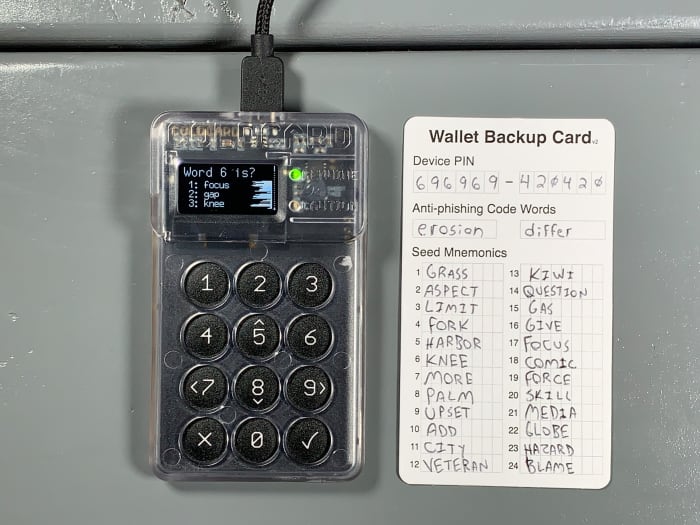
Now you will be presented with a new list of 24 words. Write these words down on your notecard. Then, double check your work.
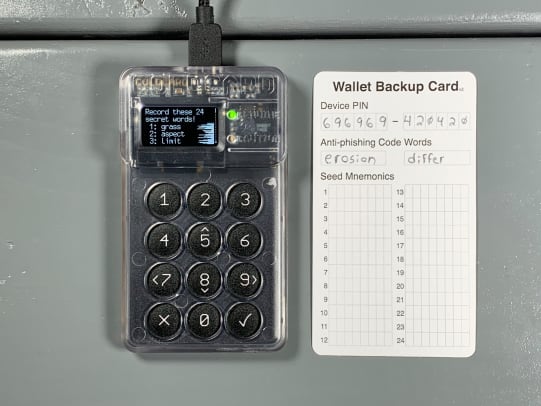
Next, you will be asked to take a test to prove you wrote the words down correctly.
You will be asked to take a test to prove you wrote the words down correctly.
After passing the test, you will be at the Coldcard’s main menu.
If you do not wish to add a passphrase, skip ahead to Step Seven: Splitting The Seed Phrase With Seed XOR.
Step Six: Creating A Passphrase
From the main menu, select “Passphrase,” then you will see a short explanation that warns you about how passphrases are not recoverable, so if you lose your passphrase then you will lose access to your funds. It also warns you that any passphrase you enter will generate a completely separate wallet.
After reading through the warning, select “OK” to continue, then you have a few options of passphrases you can enter:
Choose any assortment of characters, for example: h&v03kNUU6768%6JChoose from lowercase words, for example: comic hazard glazed madagascarChoose from uppercase words, for example: DIFFER MEDIA MORE GRASSChoose any assortment of numbers, for example: 1948568742364521Choose any combination of any of the above, for example: h&v03comicDIFFER194856
You can make your passphrase whatever you want. Just keep in mind that if you lose it, you lose your bitcoin. Keep in mind too that it may not be you recovering your funds, it might be your spouse or child or someone else, so think about how complex your security model is and if they will be able to use it if you were gone.

Once you have entered the passphrase you want, select “APPLY,” then you will be presented with the new wallet fingerprint. It is important to write this fingerprint down so that you can always verify that your passphrase was entered correctly. Then hit “OK” to enter this new wallet.
Hit “OK” to enter this new wallet.
At this point, I recommend double checking your work by trying to regenerate this fingerprint in another wallet by importing your 24 words and then applying the passphrase. If you have properly documented everything, then you should be able to get the same fingerprint from the other wallet.
For example — and please take into consideration the implications this may have on keeping your wallet fully air gapped — use Sparrow Wallet in offline mode and preferably with WiFi turned off and your network cable disconnected from the desktop.
Don’t save the wallet unless you want a second instance of your Coldcard wallet on your desktop. Or, if you do create and save a wallet file, then you can always navigate to C:UsersYourUserNameAppDataRoamingSparrowwallets and delete the wallet file from there. You just want to be careful about having any second instance of your wallet.
Alternatively, you could also perform this check with your Coldcard by navigating to “Advanced,” then “Danger Zone,” then “Seed Functions,” then “Destroy Seed.” Once you have deleted your seed, then you can import it using your backup notecard and the passphrase you wrote down.
If everything went well, then you should get the same wallet fingerprint as the one you originally wrote down. The advantage to this approach is that you do not enter your seed words and passphrase on a computer, even though it was in an offline wallet and the computer was disconnected from the network, you just never know.
Once you have your recovery information written down and you are confident that it is correct by whatever means you choose, then you are ready to split the seed.
Step Seven: Splitting The Seed Phrase With Seed XOR
For a detailed explanation on what Seed XOR is and how it works under the hood, check out this resource by @BitcoinQ_A.
In my own words and as a high level explanation, with Seed XOR you can apply some math to your seed phrase that results in multiple functional, standalone seed phrases. These seed phrases can be combined later to recreate the original seed. So, imagine that you have your seed phrase and you use Seed XOR to split it into three parts — all three parts will now be needed to recreate your wallet and recover your bitcoin. If you added a passphrase to your original seed phrase, then you would need all three parts plus your passphrase in order to recover your bitcoin.
The problem this is solving for is that if you just have a 24-word seed phrase and you stamp it on a steel SeedPlate, then anyone who gains access to that plate could recover your wallet and swipe your funds. Obviously, a passphrase would also prevent this from occurring, assuming that you used a high entropy passphrase. But if you used a weak passphrase, then it could be guessed or brute forced and combined with your 24-words to steal your bitcoin.
So, with Seed XOR, you can split your seed into multiple parts, and then rest assured that if anyone gains access to any of them, then they would need all of the parts and they would need to know how Seed XOR works in order to steal your funds. And, if you used a passphrase on the original 24-words, then they would also need that. If a single plate is found then you could even have some duress bitcoin stashed on it to hopefully satisfy your attacker and live to see another day. This is an advanced level of complexity that should ensure the safety of your bitcoin in the most adversarial environment.
Some tradeoffs with this approach are that if your loved ones need to recover your bitcoin after you are gone, then they will need to be able to complete these steps. This probably means that you will need to leave them very clear instructions, but the instructions themselves then become another piece of information you need to secure because if an adversary found your instructions, then they could follow them to steal your bitcoin assuming they are able to locate all of the steel plates.
Which brings up another trade off: depending on how many pieces you split the seed into and whether you used a passphrase or not, you can wind up with several pieces of critical information that you need to secure in order to recover your bitcoin.
Imagine that you have three plates and a passphrase and instructions for your family — that is five pieces of information that you must ensure are secure. Securing them all in the same geographic location could be problematic if you are ever threatened with your life during a robbery and the attacker is incessant on there being more bitcoin, or if there is an environmental catastrophe like a flood that sweeps everything away. Four of those five pieces would be absolutely necessary to recover the bitcoin and that is with the assumption that it is you recovering the bitcoin. If it is your family, then they would need all five pieces, otherwise all could be lost.
There is a lot to think about with threat models and recovery schemes. I recommend you weigh your options carefully and think about your setup for multiple days before deciding on one. Try to consider all of the tradeoffs you can think of, talk to your loved ones and maybe even try stepping through some processes with them to get a gauge for how well these concepts click with them. If Seed XOR solves a problem for you and the tradeoffs are acceptable then here is how it works.
Navigate to “Advanced,” then “Danger Zone,” then “Seed Functions,” then “Seed XOR,” then “Split existing.” Then you will see a short description of what you are about to do with the option to split your seed into two, three or four parts.

You have the option to use a deterministic split or a random split. The deterministic split will produce the same sub parts every time you split your seed, the resulting 24-word lists will be the same words each time. With the random split option, you will get different 24-word lists each time you split your seed.
The consideration to make here is that if you combine your deterministic sub parts into the original seed and then split it again, it will produce the same sub parts, which means that an informed adversary could conclude that there are missing sub parts if the results are different than the parts they have available or conclude that the original split was done randomly.
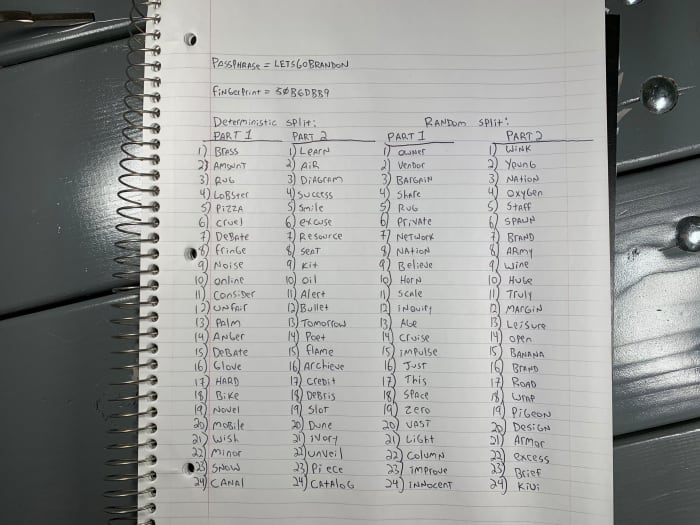
In this example, I split the original seed into two parts. Once the seed is split, the Coldcard will present two lists of 24 words each. Record both lists and double check you work. The Coldcard will display the 24th word of your original seed, which is recommended to keep documented as a checksum to verify proper reconstruction later. Then, the Coldcard will test you on the 48, 72 or 96 words.
Here are the results I got when splitting the seed deterministically and randomly into two parts:
The results I got when splitting the seed deterministically and randomly into two parts.
To verify your work, you can navigate to “Advanced,” then “Danger Zone,” then “Seed Functions,” then “Seed XOR,” and finally “Restore Seed XOR.”
There will be a short dialog presented that explains you already have a seed stored on your Coldcard and that if you reconstruct a seed from Seed XOR parts, the resulting seed will not be saved to the secure element. So, if this was an actual reconstruction and not a verification exercise, then you would probably be working with a blank Coldcard, but this would be something to consider in the situation where you already have another seed existing on the Coldcard.
In this exercise, you will have the option to include the Coldcard’s stored seed with the Seed XOR reconstruction. I would recommend choosing not to include it because it is the seed being reconstructed, so including it as a part of the reconstruction will produce a different wallet than the original one.
I had chosen to destroy the original seed on the Coldcard for this example to simulate a Seed XOR reconstruction on a new and blank Coldcard. I would only recommend destroying your seed if you know what you are doing and are 100% confident in your chosen backup method.
For example, if you look closely at the photo above, I made a mistake on deterministic split, part two, word 16. I wrote down “archieve,” which isn’t a word at all. This caused me a massive headache trying to figure it out and it was only because I had the original seed written down on the notecard that I was able to import that seed, split it again, and then double check the words I had written down.
So, make sure you are double checking all of your work and then verifying that the backup information actually works before you deposit any bitcoin or destroy any records of the original.
To restore from Seed XOR on a new or blank Coldcard, navigate to “Import Existing” then “Seed XOR.” You will see a short description that informs you all parts are needed and that the Coldcard has no way of knowing if the reconstructed seed is correct or not.
For reconstructing either the deterministic or random split, select the first 23 words from part a in order, then the Coldcard will present a short list to choose the 24th word from as it is a checksum with limited possibilities. Repeat the process for part b. Then, the Coldcard will show you what the 24th word of the resulting seed phrase would be if you stopped at this point with the two pieces.

If you have more pieces, you can continue entering them until completion. Once you have entered all pieces and the resulting 24th word is what you expect, then hit “OK” and the Coldcard will load that seed. Remember, if you already had a seed loaded on your Coldcard prior to reconstruction, then the seed resulting from the reconstruction will not be saved to your Coldcard. Only if you were importing a seed on a Coldcard that didn’t have one stored will the resulting reconstruction be loaded and saved on the secure element.
That is how you can use Seed XOR with your ColdCard, and here is what Seed XOR is doing cryptographically:
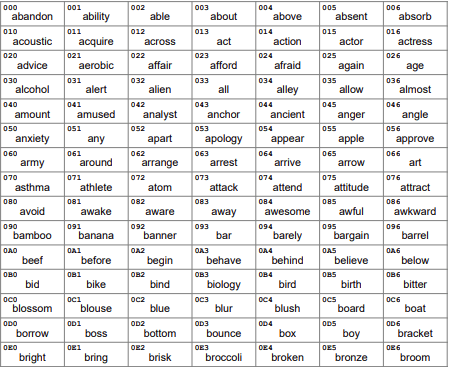
When combining two seeds together to restore your original seed, every word from your 24-word seed phrases gets converted into a three-digit hex sequence, for example:
Source: https://seedxor.com/files/wordlist.pdf
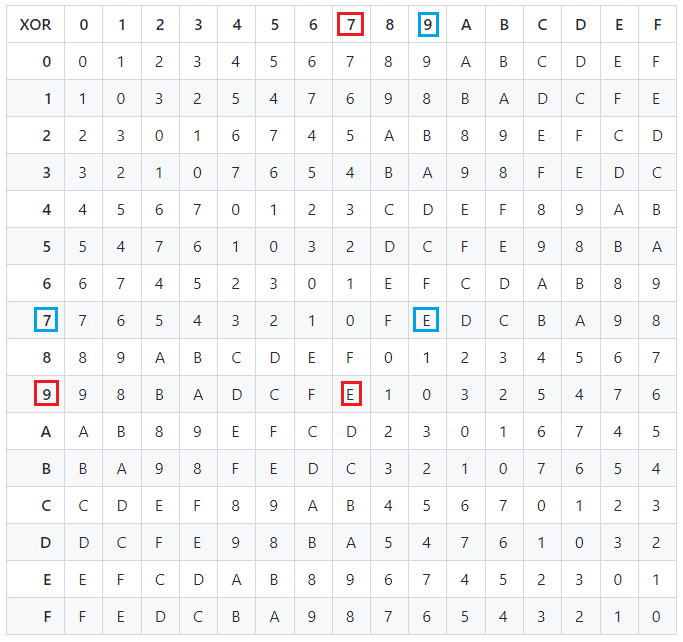
Then the hex values get combined using a table that makes it so that it doesn’t matter which order they are combined in. For example, using the table below, let’s say the first two hex sequences we are combining start with “7” and “9.”
Looking at the red squares, if you follow the columns to “7” then go down to row “9,” then you arrive at “E.” Likewise, looking at the blue squares, if you start with row “7” and go across to column “9,” then you again arrive at “E.”
Source: https://seedxor.com/files/worksheet.pdf
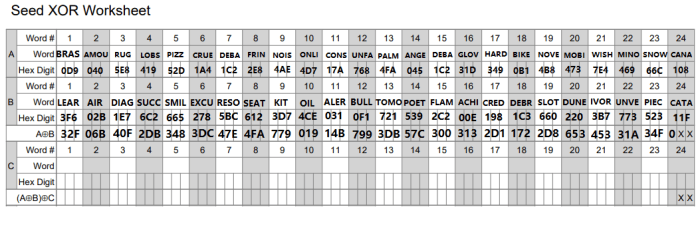
Using this method, we can see that the first words on my deterministic split resulting seed phrases are “BRASS” and “LEAR,” which equate to “0D9” and “3F6” in hex. By combining these two hex values on the Seed XOR table, we arrive at “32F,” which equates to “GRASS,” the first word from my original seed phrase.
Here are both of my deterministic seed phrases converted to hex values and then combined. This worksheet can be downloaded as a .pdf here.
Both of my deterministic seed phrases converted to hex values and then combined.
Taking the values from the A⊕B row and using the seed-word-to-hex conversion table, you can see that the original seed has been reconstructed:
You can see that the original seed has been reconstructed.
Now, you may have noticed that this is only 23 words, not 24.
In all BIP39 seed phrases, the last word acts as a checksum and it can be calculated with the first 23 words. The Seed XOR math does not use these last 8 bits that make up the checksum. This is why it is advisable to save the 24th word from your original seed phrase so you can ensure you have recreated the correct one upon reconstruction.
Alternatively, you can type the 23 words into a Coldcard through the import seed phrase option and the Coldcard will generate a short list of possible 24th words. This would narrow down your choices, but if you don’t recall which one it was then this approach could cost you a considerable amount of time in recovering your bitcoin as you would have to try one, enter that wallet, export the xpub, import it to another wallet, and scan it for your transactions.
If it is empty, then you will have to do the process over again and try the next word on the list. Not impossible, but not ideal either. Keep record of your original seed’s 24th word to avoid this last resort.
Now that you are sure your backup information works and you understand how the math works, you can secure this information on a robust medium like stainless steel.
Step Eight: Steel Recovery Plates
Steel plates offer a simple solution for securing your recovery information in a medium that can withstand environmental hazards such as fire and flooding. The basic idea here is that we will take the two BIP39 seed phrases split from the original seed phrase and imprint those on their own steel plates. Then these two steel plates will be needed to reconstruct the original seed phrase.
Another benefit is that both of the steel plates can be funded with an amount of duress bitcoin and this can be used in a plausible-deniability scheme, so long as your attacker doesn’t know how Seed XOR works and doesn’t know that multiple BIP39 seed phrases can be combined and that they should pressure you for more information or other backup seed phrases.
The steel plates can be stored as a secret in the open since alone, none of the split pieces can access your original funds. There is still benefit in storing the plates in separate geographic locations and also concealing them securely.
You will notice that the plates have the alphabet running vertically on the first column and that there are twelve numbered sections, one through 12, that each contain four columns. If you flip the plate over, the sections are numbered 13 to 24. Each section will get stamped with the first four letters of each seed word. Only the first four letters are necessary to recover the word since no two words on the BIP39 word list have the same sequence of initial four letters.
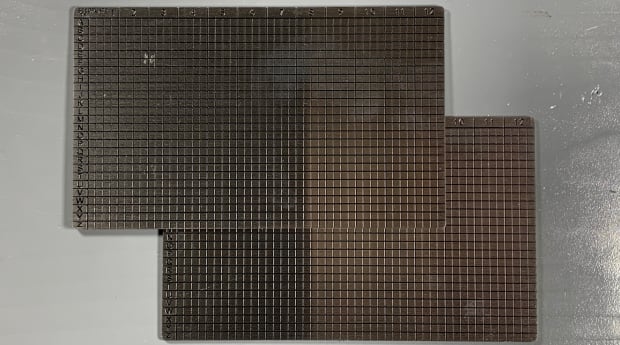
Start with a permanent marker so you can double check your work before making the markings with the spring-loaded punch. If you make a mistake with the marker, you can use acetone to clean it off.
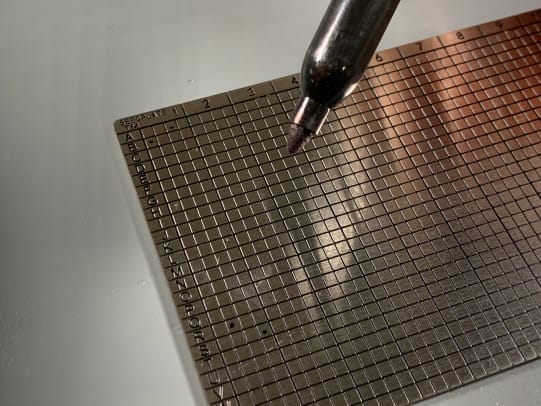
Use the spring-loaded punch to stamp the marks on both sides of the plate.

These plates provide a robust medium of secure storage against the elements, fire and flooding.
Once you have your seed phrases stamped on the steel plates and you know that your backups can reconstruct your original seed, then you can destroy the handwritten seed phrases you made while setting up your wallet by safely burning them.
Thanks for reading! I hope this guide has helped you get a Coldcard setup and has given you some food for thought on ways in which you can secure your backup information that provides you with plausible deniability and a robust, stainless-steel storage medium.
This is a guest post by Econoalchemist. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
Source link
#Protect #Bitcoin #Coldcard #Integrated #Seed #XOR