zk-SNARKs on Bitcoin: Run Zcash on Bitcoin

This post was first distributed on Medium.
Previously, we have demonstrated one realizes some numerical mystery utilizing zero information evidence (ZKP), without uncovering the mysterious itself. The mysterious information include:
While helpful in their particular applications, these ZKPs can’t be applied to erratic numerical capabilities. Conquering these impediments, a zk-SNARK (zero-information Succinct Non-intelligent ARguments of Knowledge) is a convention intended to produce a ZKP for any numerical capability. The created verification is “succinct” and “non-interactive”: a proof is two or three hundred bytes and can be confirmed in steady time and inside a couple of milliseconds, without expecting to pose extra inquiries of the prover. Together, these properties make zk-SNARK particularly reasonable for blockchains, where on-chain capacity and calculation can be costly and shippers frequently go disconnected subsequent to sending an exchange. Mysterious digital money Zcash and the brilliant agreement stage Ethereum are among its outstanding early adopters, among others.
zk-SNARK
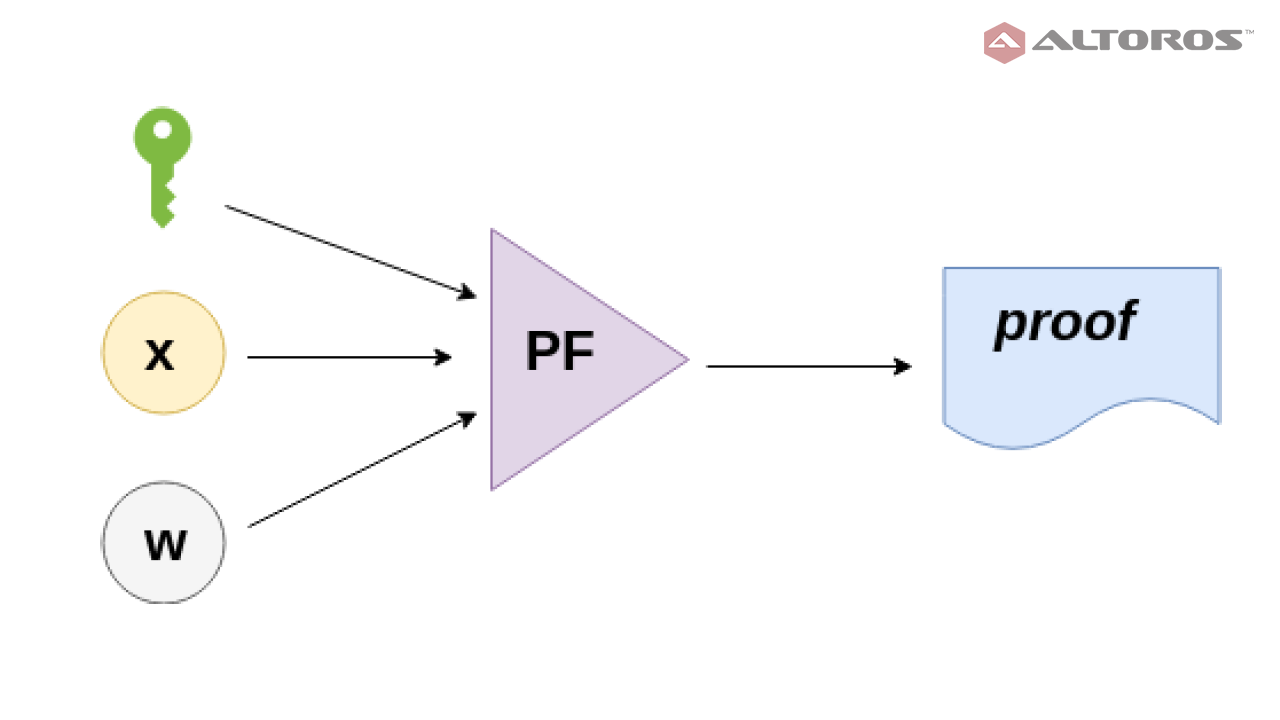
A zk-SNARK comprises of the accompanying three calculations: G ,P, andV.
Generator (C circuit, λ is 
(pk, vk) = G(λ, C)
Prover (x bar inp, w sec inp):
π = P(pk, x, w)
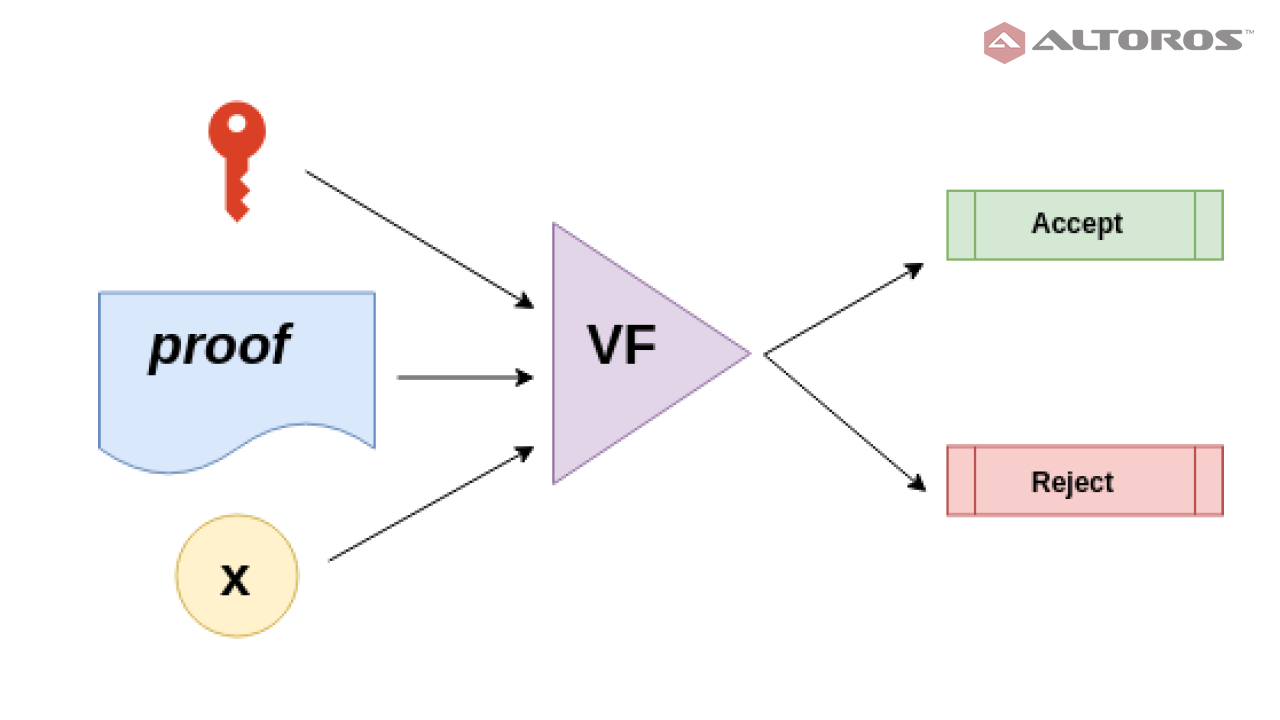
Verifier:
V(vk, x, π) == (∃ w s.t. C(x,w))
— Christian Lundkvist (@ChrisLundkvist) November 19, 2016
Key Generation
A key generator G takes a mysterious boundary λ and a capability C, and produces a demonstrating key pk and a confirmation key vk. Both keys are made public.
C is a boolean capability (likewise called a program or circuit) that takes two sources of info: a public info x and a confidential information w (otherwise known as, witness). For instance, C can be a capability that checks assuming that w is the sha256 preimage of the overview x.
C(x, w) = sha256(w) == x
Prover
The prover P takes as info the demonstrating key pk, a public information x and a confidential observer w to deliver a proof that the prover knows an observer w that makes C(x, w) assesses to true.
Verifier
The verifier V takes confirmation key vk, the evidence, and the public information x and acknowledges the evidence provided that it is created with the information on witness w¹.
Implementation
When zk-SNARKs are utilized in blockchains, both the key and evidence age are executed off-chain. Just the overall check calculation is run inside a shrewd agreement on chain.
There are various plans of zk-SNARKs in the writing. We execute the most generally utilized plot Groth16 because of its small proof size and fast verification.
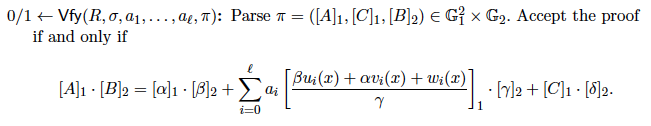 Verifier in Groth16: page 18
Verifier in Groth16: page 18
The full code is recorded beneath, in light of our elliptic curve arithmetic and pairing libraries.
Contract ZKSNARK
It is quite significant that the verification size (Line 23-27) and the quantity of pairings (Line 43-44) are steady, paying little mind to how complex the capability C being demonstrated is.
Summary
zk-SNARK is a strong crude for blockchain protection and versatility. Today we just showed what zk-SNARK is and how to execute it on Bitcoin. We will investigate how to involve it sooner rather than later. Why and how it functions inside, which is very math weighty, is past the extent of this single article. There are numerous magnificent instructional exercises, for example, this series and this paper.
***
NOTE:
[1] There is an exemption. Anybody knows the mysterious boundary λ utilized in the generator can produce counterfeit yet substantial evidence without information on witness. For that reason it is called harmful material. It should be disposed of after the confided in arrangement phase.
Watch: The BSV Global Blockchain Convention show, Smart Contracts and Computation on BSV
New to Bitcoin? Look at CoinGeek’s Bitcoin for Beginners area, a definitive asset manual for dive more deeply into Bitcoin — as initially imagined by Satoshi Nakamoto — and blockchain.
Source link
#zkSNARKs #Bitcoin #Run #Zcash #Bitcoin